OIG Special Report Common Cybersecurity Weaknesses – Unclassified Information on Contractor Networks

Key Details: on November 30, 2023, the Department of Defense (DoD) Office of Inspector General (OIG) issued a Special Report titled “Common Cybersecurity Weaknesses Related to the Protection of DoD Controlled Unclassified Information on Contractor Networks”. This Special Report aims to provide information on the common cybersecurity weaknesses defense contractors face that was identified in OIG audit reports. Defense contractors are encouraged to thoroughly review this Special Report before attesting compliance with National Institute of Science and Technology (NIST) SP 800-171.
Ryan & Wetmore is positioned to take your government contracting business to the next level. From accounting system compliance assistance to forecasting and growth strategies, Ryan & Wetmore has the right tools to assist you. Contact us today to learn more.
Report Background
The DoD OIG issued 5 audit reports between 2018 and 2023 that analyzed contractors’ implementation of and compliance with federal cybersecurity requirements. This focused on the protection of Controlled Unclassified Information (CUI) under NIST SP 800-171. Compliance with NIST SP 800-171 helps reduce the risk of cyber-attacks and incidents and prevents the loss of sensitive DoD data. As such, this Special Report aims to equip DoD Contracting Officers with focus areas when assessing contractor performance and defense contractors with key areas to review before attesting compliance with NIST SP 800-171. Additionally, an assessment under the NIST SP 800-171 DoD Assessment Methodology may be required before contract award or during the contract period. This assessment methodology provides an objective opinion on NIST SP 800-171 compliance. Therefore, defense contractors are encouraged to fully review the weaknesses identified in the Special Report and to implement updates to their cybersecurity infrastructure as needed.
What is Controlled Unclassified information?
CUI refers to information that is generated or held for the government that requires safeguarding or dissemination controls per relevant laws, regulations, and government-wide policies. CUI differs from classified information as outlined in Executive Order 13526 Classified National Security Information.
The purpose of CUI is to create a unified effort between various federal agencies to standardize CUI safeguarding practices. Federal agencies also retain the responsibility to safeguard CUI when shared or utilized by contractors during contract performance. As such, contractors must ensure a comparable level of protection when handling, storing, or transmitting, CUI.
What is NIST SP 800-171?
NIST SP 800-171 is a publication regarding security requirements and practices when handling CUI in contractor networks. The NIST first published this standard in 2015. Since then, SP 800-171 has received updates to better align with the changing technology and cybersecurity ecosystem. The purpose of SP 800-171 is to define practices and procedures for contractors to safeguard CUI. Contractors should note that SP 800-171 is only applicable to the networks within the contractor’s system that handles CUI. Contractors must also develop a plan and implement the 110 controls under SP 800-171. The table below summarizes the 110 requirements in 14 categories shown in the Special Report.
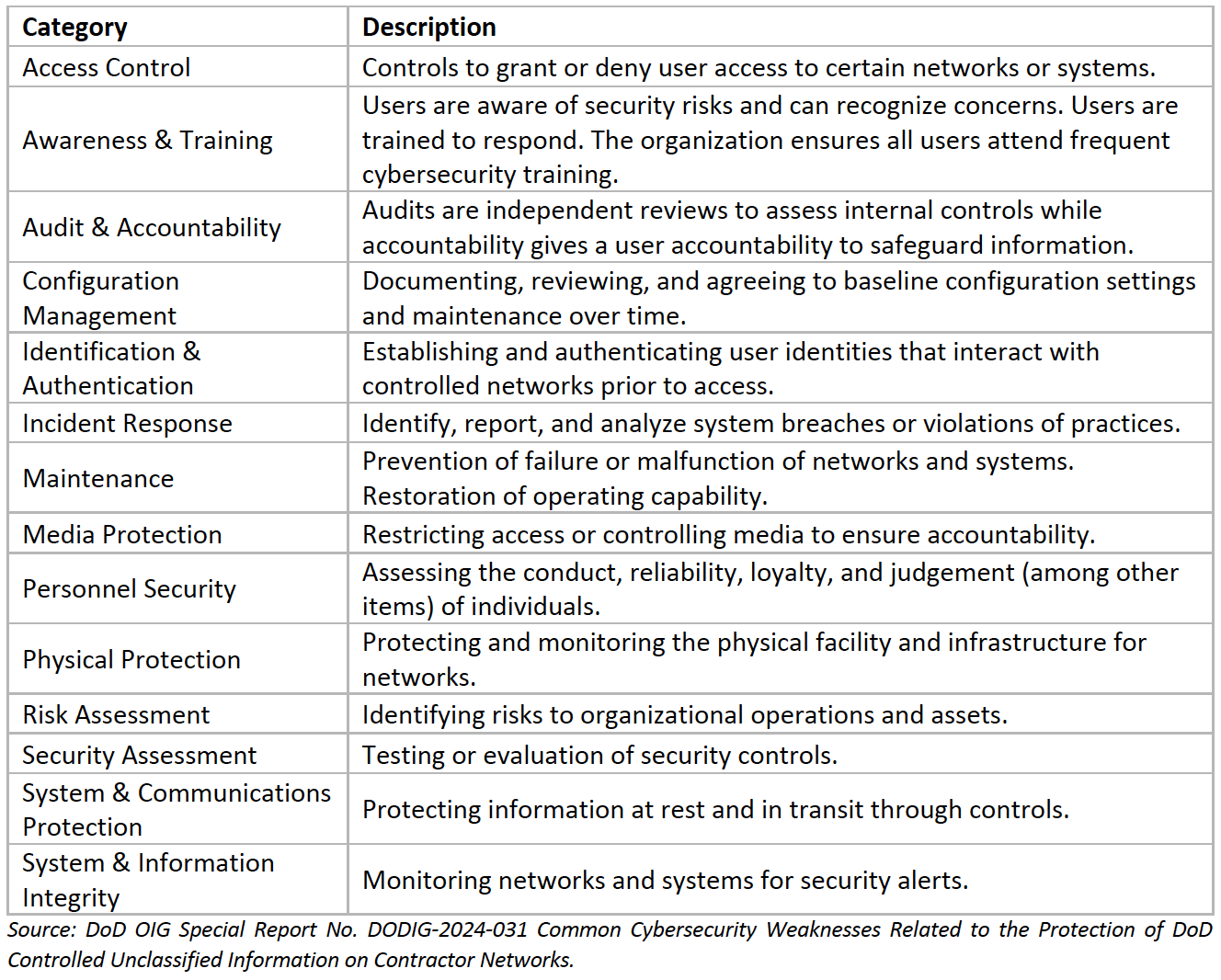
Weaknesses Identified in the Special Report
From 2018 to 2023, DoD OIG issued 5 audit reports regarding defense contractor’s implementation of NIST SP 800-171 controls relating to CUI. Below lists the weaknesses identified in the report issued. Defense contractors are encouraged to review their cybersecurity infrastructure, internal controls, and practices to determine and maintain compliance.
- Networks are not locked after inactivity and system activity is not generated or reviewed.
- Strong passwords and multifactor authentication are not enforced.
- User accounts are not disabled during extended inactivity and physical security controls are not used.
- CUI is not protected, and networks are not scanned for viruses.
- Access to facilities is not controlled and configuration settings are not monitored.
- Incidents are not tracked, documented, or reported.
Prepare Ahead
Cybersecurity is becoming a large focus in today’s contracting marketplace. Contractors should aim to have a dedicated cybersecurity plan with resources geared towards monitoring potential security risks. Defense contractors are also encouraged to thoroughly review the report, above weaknesses, and NIST SP 800-171 controls to ensure compliance and to review the following steps to stay ahead:
- Conduct an internal review to determine your overall cybersecurity health.
- Analyze your incident detection, reporting, and response plans and whether internal controls are documented and in place.
- Review your contracts and related agreements with subcontractors to ensure any flow down requirements are in place.
- Identify gaps in defenses and invest in capabilities that improve security. This can include investing in employee training or service providers.
- Understand and provide training on the most common cybersecurity threats such as phishing attempts, malware, viruses, ransomware, and spyware.
- Ensure your networks are secure and that you have updated antivirus software.
- Monitor any cloud service provider accounts and enable multi-factor authentication.
- Analyze your company’s capture strategy and pipeline of future contracts. Identifying the requirements of the future will enable your company to prepare ahead of time.
- Review the requirements under CMMC 2.0 and understand the compliance level required of your company. See our article here for more information.
- For more information on NIST SP 800-171, see our article here.
For further information and expertise, contact Ryan & Wetmore today.
Today’s Thought Leaders

About Peter Ryan
Partner, Co-founder, & CPA
Peter T. Ryan co-founded Ryan & Wetmore in 1988 with business partner Michael J. Wetmore. Peter provides clients with the best strategies for success. His expertise extends across various industries. Peter obtained a Master of Business Administration in Finance from the University of Baltimore and a Bachelor of Arts in Accounting from the Catholic University of America.

About Rosie Cheng
Finance Consultant
Rosie Cheng is a Finance Consultant at Ryan & Wetmore. She focuses on government contracting services and produces many of the firm’s government contracting newsletters. Rosie graduated from Georgetown University with a Master of Science in Management and from William and Mary with a Bachelor of Business Administration.


