Government Contractor 2023 Cybersecurity Landscape – What to Know (Part 2 of 2)

Key Details: Cybersecurity regulations, requirements, and forthcoming implementations are set to spark a pivotal year for the government contracting community. From the Cybersecurity Maturity Model Certification (CMMC) to the National Institute of Standards and Technology’s (NIST) announcement of framework revisions, 2023 will greatly impact all aspects of the cybersecurity landscape for government contractors. As there are several regulations that are set to be implemented or are expected to be updated, government contractors are encouraged to stay ahead by fully understanding the requirements they may be subject to and conducting an internal review relating to cybersecurity health. For Part 1 of this series, click here or contact Ryan & Wetmore for more information.
Key Regulations Government Contractors Should Look Out For
The items below contain the key cybersecurity regulations that government contractors should be aware of in 2023. Please note that this list is not exhaustive. As such, contractors are encouraged to thoroughly review and understand the upcoming and changing regulations that may impact their business.
- NIST announcement of intent to revise the Cybersecurity Framework
- New National Cybersecurity Strategy
For information regarding CMMC 2.0, the revision of NIST SP 800-171, and the Department of VA’s final rule, check out Part 1.
NIST Announcement of Intent to Revise the Cybersecurity Framework
Earlier this year, NIST released their concept paper for the Cybersecurity Framework (CSF) 2.0 that includes potential significant updates for contractors to keep track of. The current CSF is based on existing standards and practices that are widely used by both the public and private organizations. As such, the CSF is undergoing a refining and improvement process to align with changing cybersecurity risks and technological trends.
Potential significant changes in CSF 2.0 that will impact government contractors include the following. Contractors are encouraged to fully review the concept paper as NIST plans on increasing guidance and implementation practices.
- CSF 2.0 will relate clearly to other NIST frameworks such as the Risk Management Framework or the Secure Software Development Framework. The NIST plans to reference related frameworks as guidance in either CSF 2.0 or associated materials. This will provide contractors with easy access to the vast number of frameworks they may be required to comply with.
- NIST plans to move toward the use of an online and updatable reference for CSF 2.0.
- CSF 2.0 recognizes the importance of incidence response and will expand the consideration of outcomes in the CSF Respond and Recover Functions. As such, CSF 2.0 may include more planning outcomes and increase alignment with the Computer Security Incident Handling Guide.
- NIST is revising its Digital Identity Guidelines (NIST SP 800-63) as identity management is a critical aspect of cybersecurity. As such, NIST is exploring updates to the CSF’s Identity Management, Authorization, and Access Control Category to include potential reordering of subcategories.
- Increased and updated guidance on framework implementation as well as implementation examples for subcategories.
- A new Govern function will be added to CSF 2.0 that emphasizes cybersecurity risk management and government outcomes.
- CSF 2.0 aims to emphasize the importance of supply chain risk management as well as provide an advanced understanding of cybersecurity measurement and assessment.
NIST provided the following timeline for the development and implementation of CSF 2.0. Interested parties and impacted contractors are encouraged to stay tuned, review drafts, and attend working sessions to gain a full understanding of the scope of CSF 2.0.
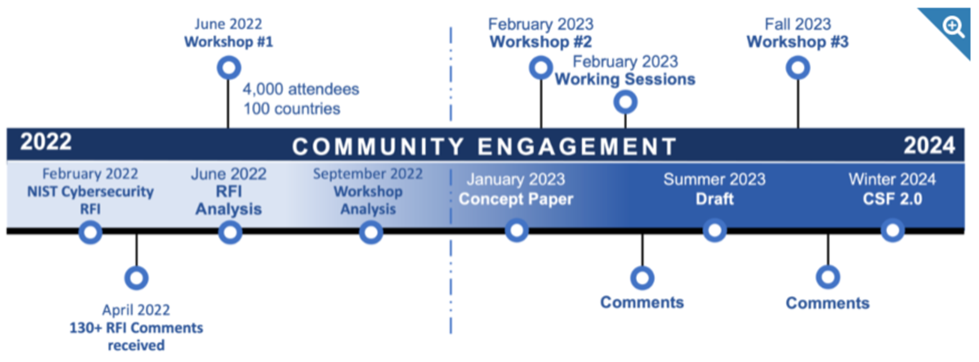
https://www.nist.gov/cyberframework/updating-nist-cybersecurity-framework-journey-csf-20
New National Cybersecurity Strategy
On March 3rd, 2023, the White House released the National Cybersecurity Strategy (NCS) to secure the cybersecurity ecosystem by focusing on leveraging existing mechanisms to bolster cyber resilience. The NCS is built around 5 key pillars and is set to rebalance responsibility to defend cyberspace and realign incentives to favor long-term investments. The 5 pillars and associated strategic objectives are as follows:
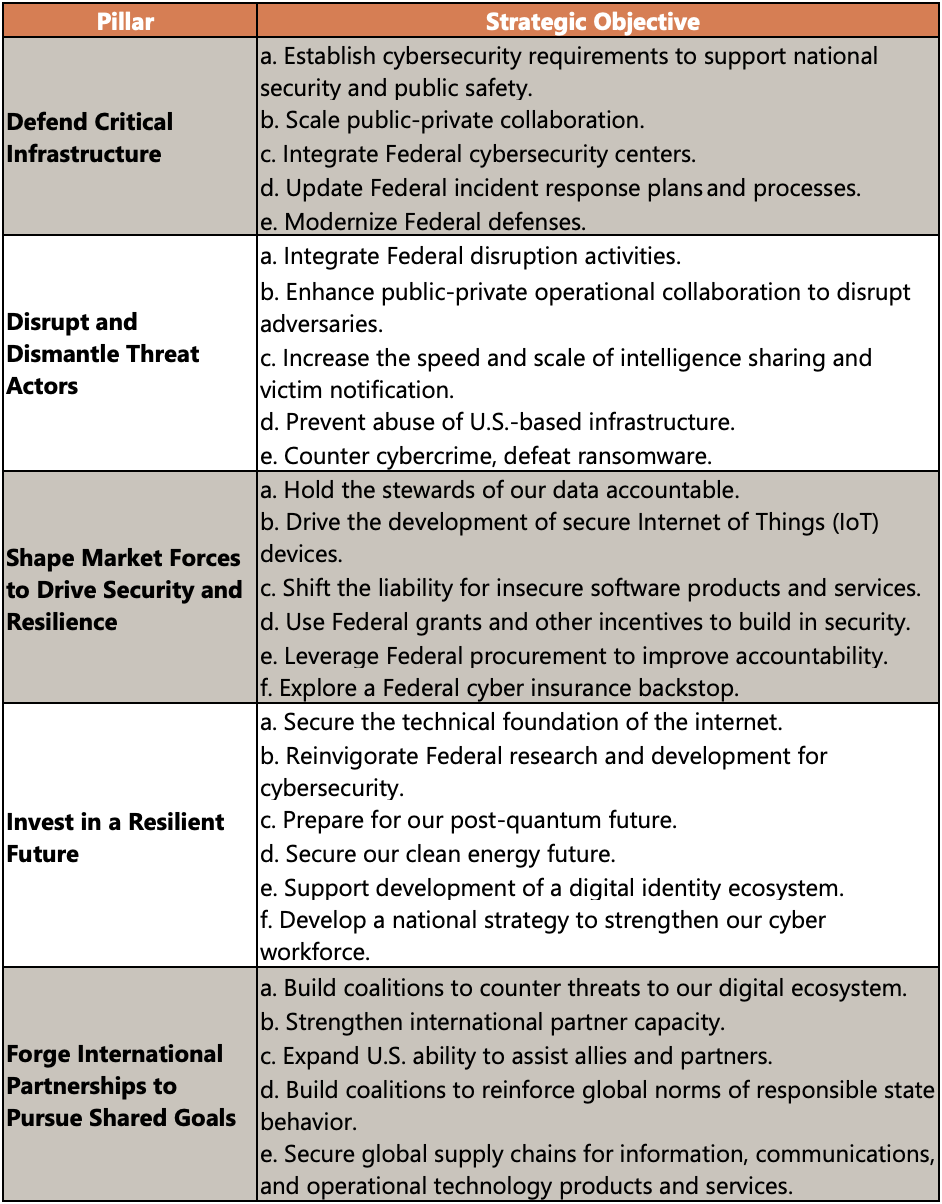
Businesses are encouraged to thoroughly review the NCS as shifts in responsibility and accountability alongside heightened cyber awareness brings forth new compliance requirements.
Conclusion and Action Plan
The 2023 cyber ecosystem will see a wide variety of updates, enhancements, and shifts as Federal agencies continue to patch together state, sectoral, and contract rules. Contractors are encouraged to monitor the status of various regulations and follow the steps below to determine whether additional compliance measures are required:
- Understand which regulations and compliance requirements may impact your business.
- Conduct an internal review to determine your overall cybersecurity health.
- Analyze your incident detection, reporting, and response plans and whether internal controls are documented and in place.
- Review your contracts and related agreements with subcontractors to ensure any flow down requirements are in place.
- As heightened regulations continue to be introduced, it is now more important than ever to ensure you have the necessary cybersecurity defenses in place. Identify gaps in defenses and invest in capabilities. This can include investing in employee training or service providers.
- Understand and provide training on the most common types of cybersecurity threats such as phishing attempts, malware, viruses, ransomware, and spyware.
- Ensure your networks are secure and that you have updated antivirus software.
- Monitor any cloud service provider accounts and enable multi-factor authentication.
- Analyze your company’s capture strategy and pipeline of future contracts. Identifying the requirements of the future will enable your company to prepare ahead of time.
As heightened regulations continue to be introduced, it is now more important than ever to ensure you have the necessary cybersecurity defenses in place.
Today’s Thought Leaders
About Peter Ryan
Partner, Co-founder, & CPA
Peter T. Ryan co-founded Ryan & Wetmore in 1988 with business partner Michael J. Wetmore. Peter provides clients with the best strategies for success. His expertise extends across various industries. Peter obtained a Master of Business Administration in Finance from the University of Baltimore and a Bachelor of Arts in Accounting from the Catholic University of America.
About Rosie Cheng
Finance Consultant
Rosie Cheng is a Finance Consultant at Ryan & Wetmore. She focuses on government contracting services and produces many of the firm’s government contracting newsletters. Rosie graduated from Georgetown University with a Master of Science in Management and from William and Mary with a Bachelor of Business Administration.


